Custom TOTP MFA for Enterprise Identity Integration in a Private Cloud
We designed and implemented a custom TOTP MFA, or time-based one-time password (TOTP) multi-factor authentication system hosted in a private cloud. The client required complete control over user identity, login records, and device pairing without involving third-party authentication providers.
To comply with privacy regulations, storing authentication logs and user credentials outside the private cloud was unacceptable for this project, so we decided not to use solutions like Okta and Auth0.
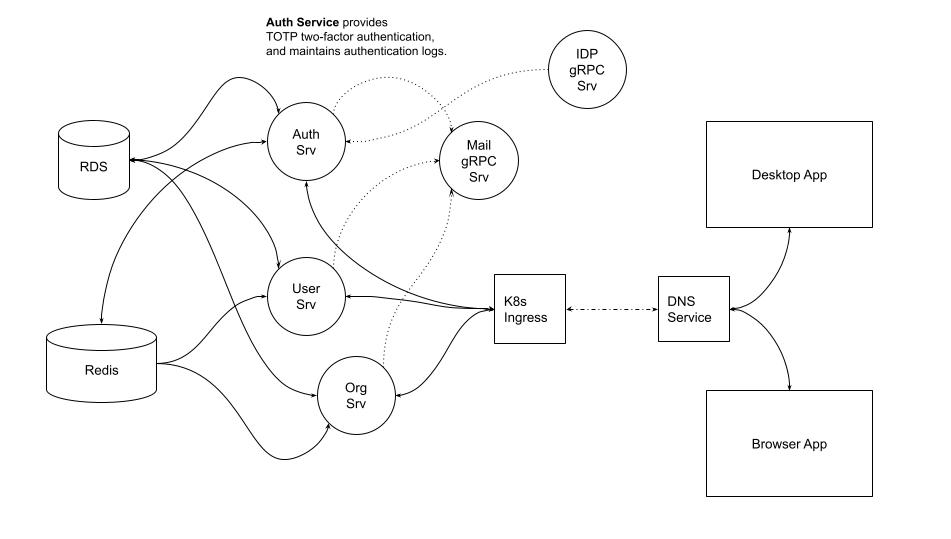
The system uses a microservices architecture that exposes REST and gRPC APIs. We deployed the architecture inside our client’s private cloud. A relational database stores user and session data, and a Redis database handles secure session caching. Authentication integrates with existing LDAP and Active Directory systems to ensure compatibility with enterprise infrastructure.
Also read: Multi-factor authentication (MFA/2FA) Methods
Why We Built Custom TOTP MFA Ourselves
We decided to build the MFA system in-house rather than integrate a third-party provider to have complete control over data residency and security. We didn’t want to store credentials or logs outside the organization’s cloud for privacy reasons. By avoiding external API dependencies, we improved latency and eliminated concerns around changing third-party SDKs. Most importantly, the UI and backend were tightly integrated with the client’s existing system, making the experience seamless for users and maintainable for the application development team.
This approach works best for organizations with strong infrastructure and strict compliance needs. It avoids the tradeoffs of outsourcing identity management to 3rd party identity providers.
Why TOTP MFA?
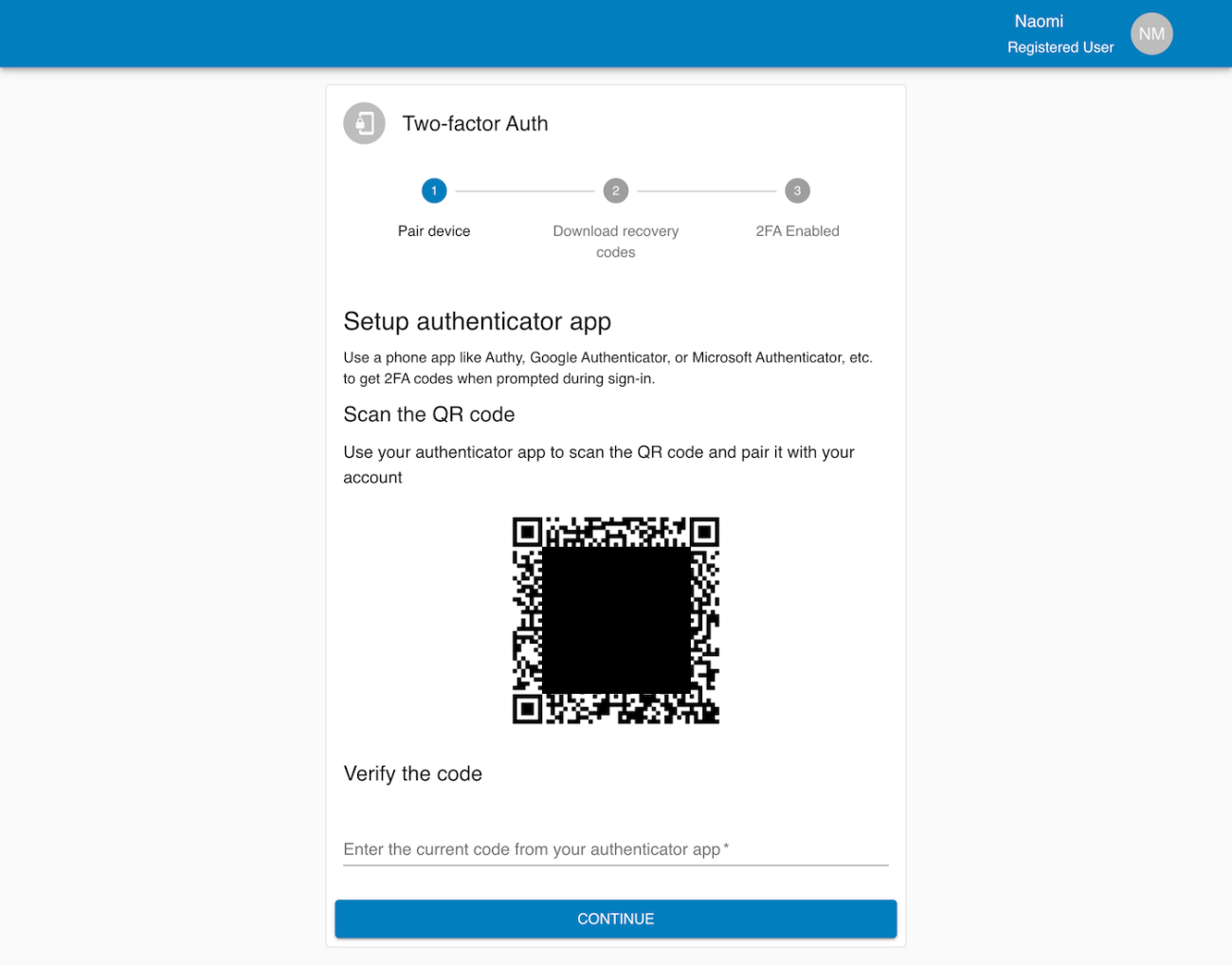
TOTP is a secure method that generates one-time passcodes on a user’s device without a network connection. It’s widely preferred in high-security applications because it doesn’t rely on SMS, email, or push notifications. Since we never exchange credentials with external services, and codes are valid for a short time window, it reduces exposure to attack. Pairing is handled securely through QR codes, and users can rely on standard authenticator apps like Google Authenticator, Microsoft Authenticator, and Authy.
What We Built a custom TOTP MFA
We integrated the TOTP system with the organization’s existing identity provider, allowing it to verify usernames and passwords using its internal directory services. The system works with both Active Directory and other LDAP-compatible infrastructures.
To manage TOTP, we implemented functionality for generating and storing encrypted TOTP secrets per user. Users can pair their device with a secure QR code and complete the process through a guided interface.
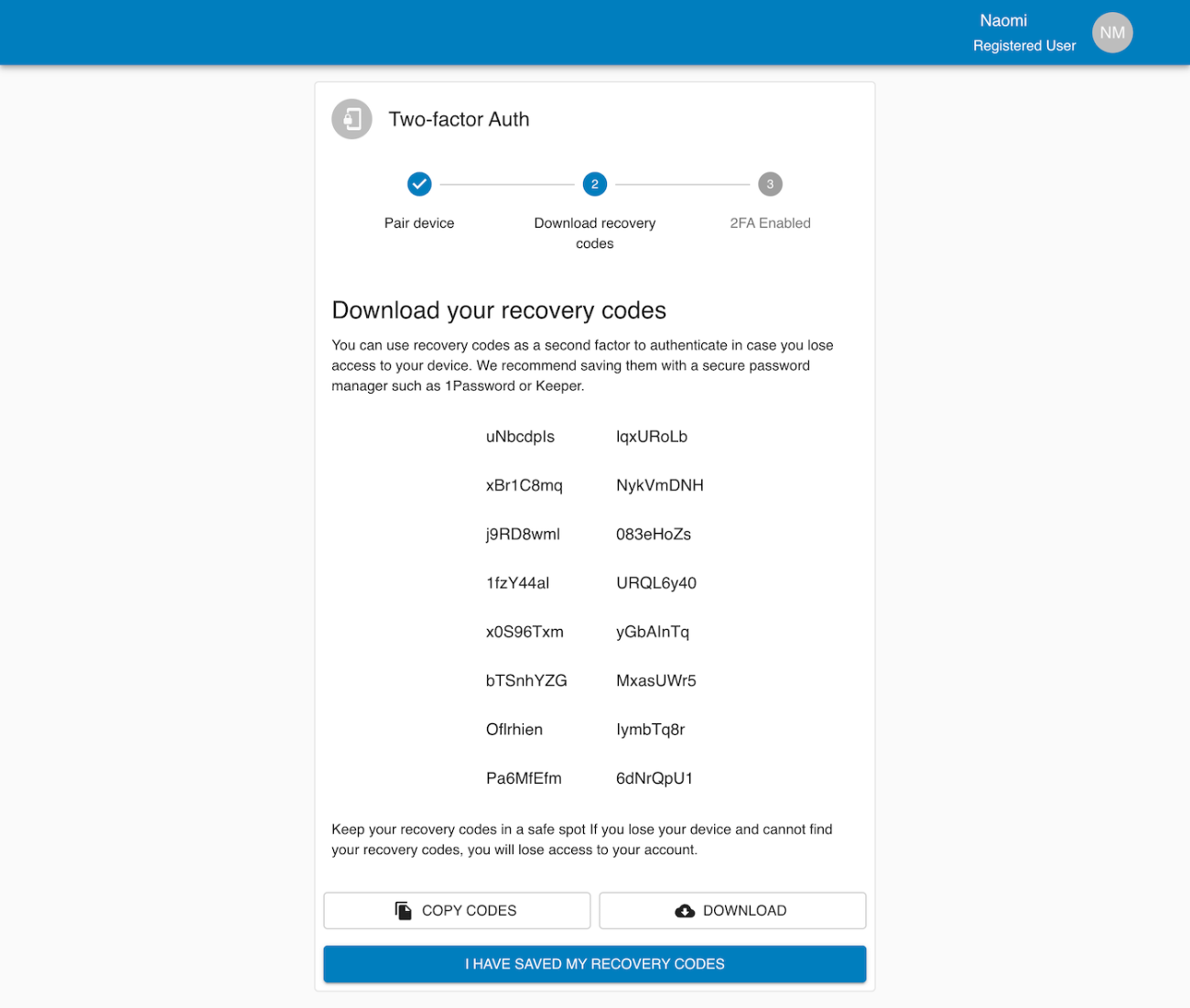
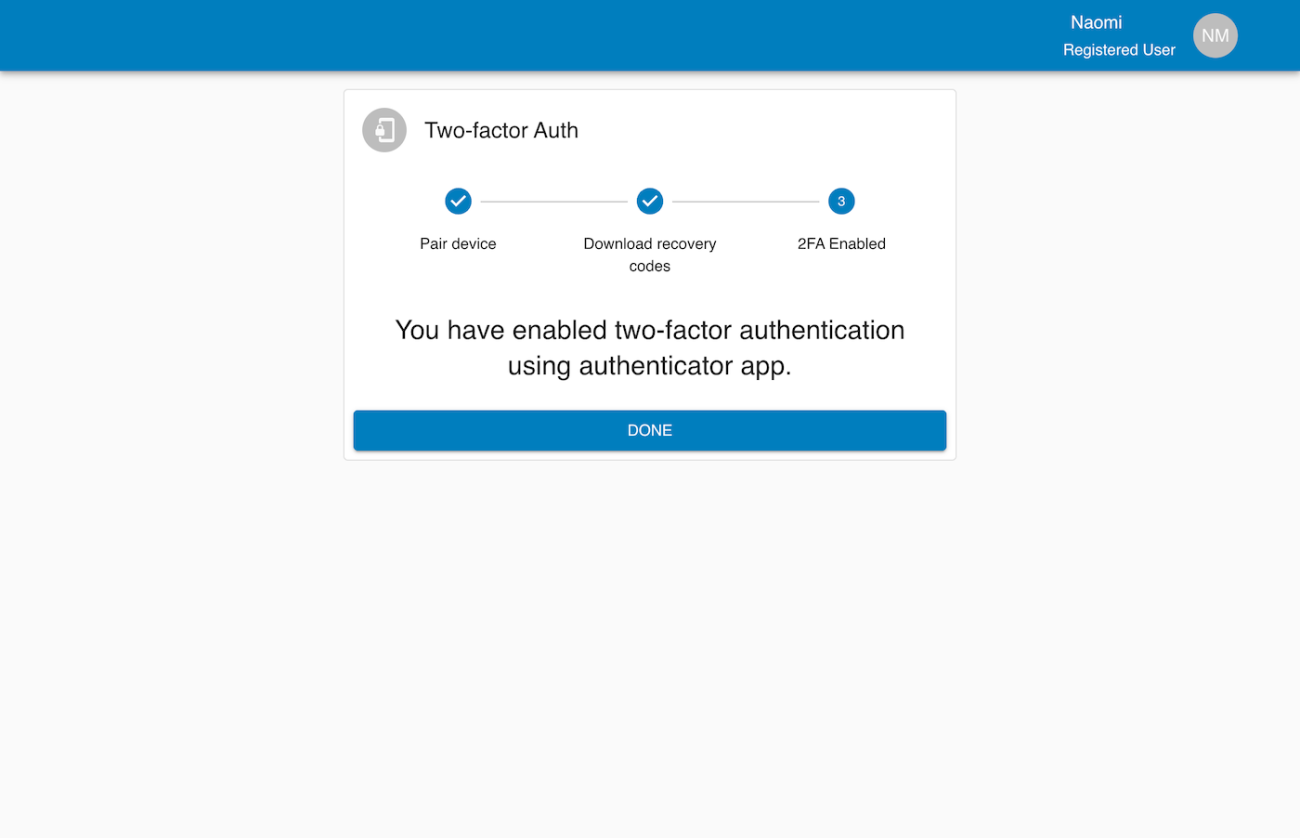
The system also includes a recovery code workflow. When users enable MFA, single-use recovery codes are generated and stored. The users can view, copy, download, or print the recovery codes if they lose access to their authenticator app. The users can use recovery codes for authentication as part of the login process.
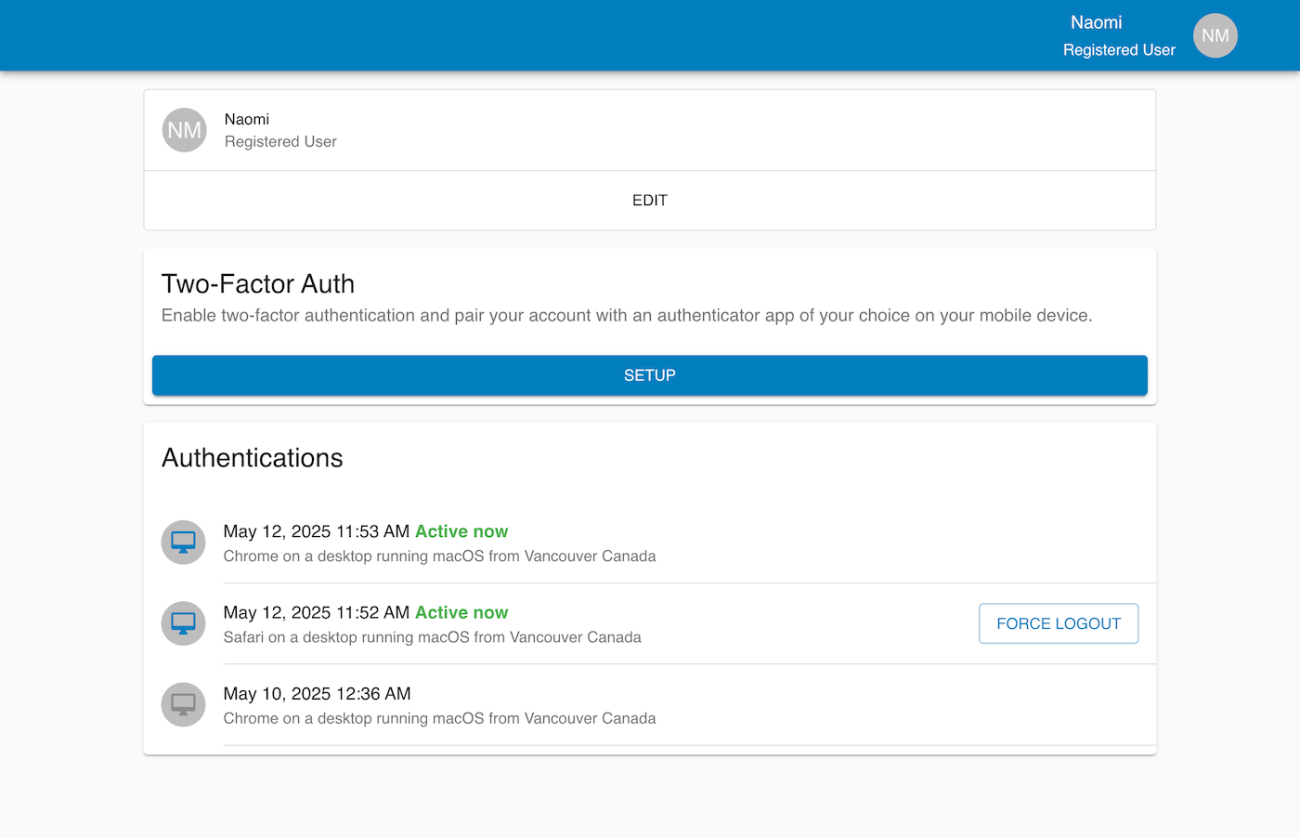
We created a logging system that tracks every login for every user within the organization. Users can see a history of their session activity and receive an email notification after each login. These emails include a timestamp, IP address, and approximate location for additional context.
On the client side, we built a seamless user experience for both web and desktop apps. The login flow includes MFA prompts, recovery fallback, and device pairing. Users can easily turn the MFA feature on or off and view active sessions. Admins can view authentication logs, revoke access, and force logout sessions.
Client-Facing UI/UX
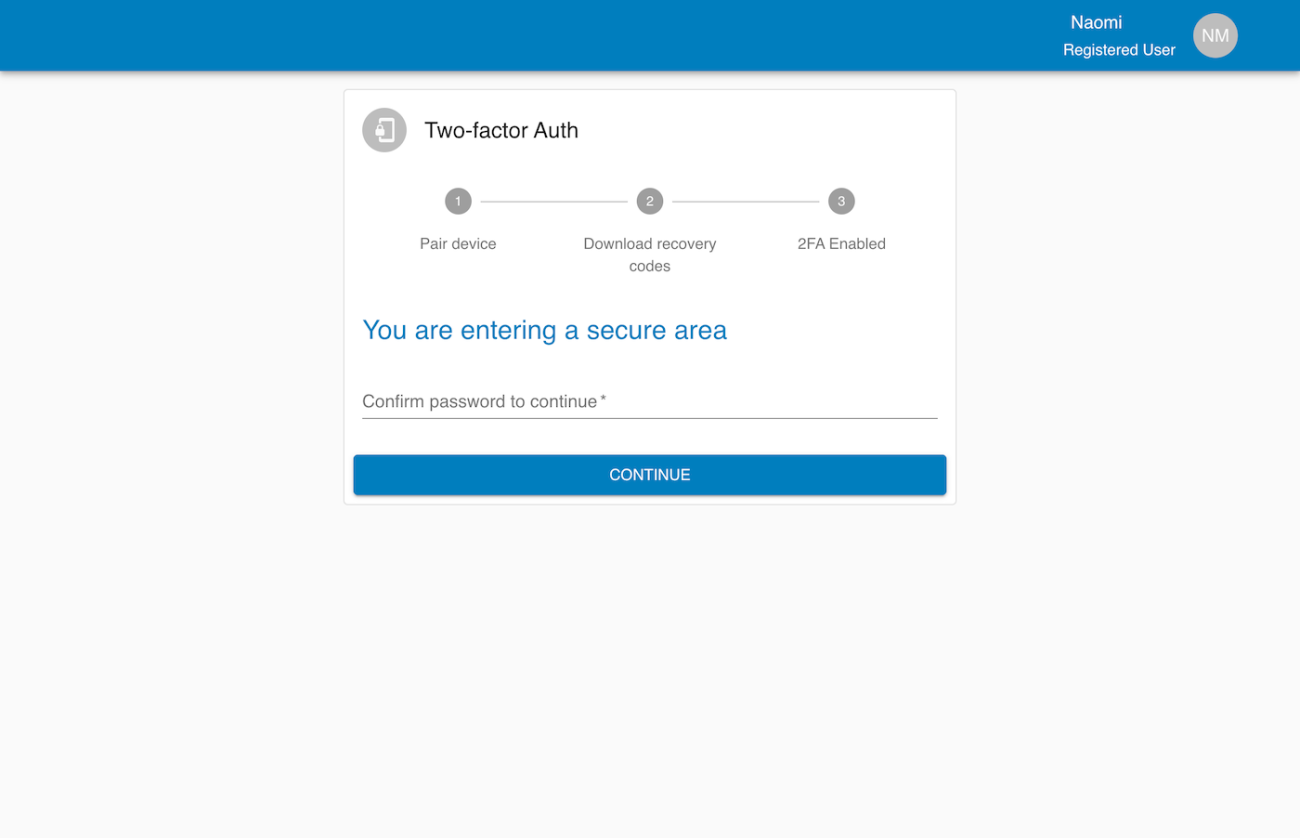
The MFA system starts with a user profile screen where the user can enable 2FA. From there, the user walks through a secure flow: reconfirming their password, scanning a QR code with their authenticator app, saving recovery codes, and finally completing the activation. Once enabled, the user’s session list appears on their profile page, and they can force log out from devices if needed.
Photo by: Sarah Pflug